ASK A SPECIALIST ;)
The lack of DDoS Protection…
What happens nowadays ?
- Every day, bad intentioned internet users find a utility of a ddos attack, being it solely for his own advantage purposes, such as : blackmailing, destroying your business reputation, dirty competition and so on.
- They act in an unscrupulous way trying to cause the most damage and downtime as possible for you, many of them doesn’t even consider this as an illegal activity, but instead, they do threat this more likely a ‘tool’ for their objectives.
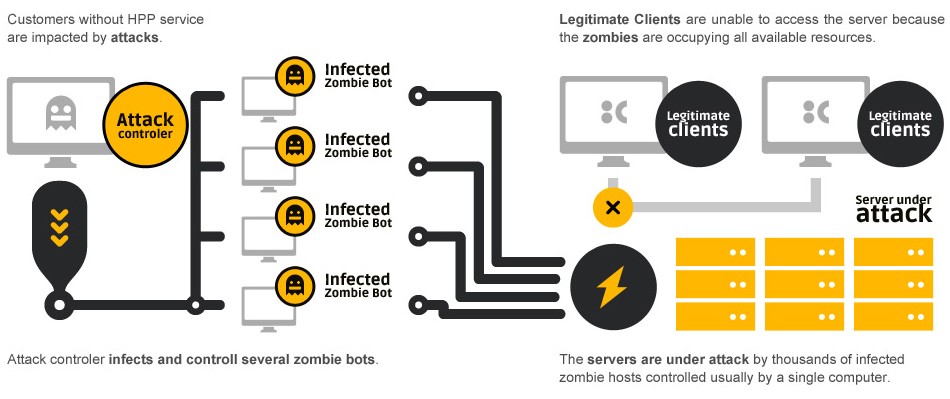
- The most common ways to attack any internet service nowadays is through the usage of ‘booters or stressers’, which are websites with paid membership where you supposedly would use it to test your own network against vulnerability or impacts under such attacks. However, they will instead of using it for the original purpose, aim towards your services, the bad traffic, causing you downtime and troubles for your business. There are also users which holds access to zombie botnets, which are a network of infected computers, generally many of them attacking you at the same time, to cause the same effect of the ‘booters or stressers’.
- In the picture shown below, you can see how your server or application is affected during a ddos attack.
What can I do about it ?
- Get protected with a good ddos protection company;
- Take preventive measures to make sure your server / application is secure;
- Tune up your system settings to ensure the highest performance;
- Get consultation about your business and allocate the need/optimum infrastructure for it;
The Solution for the Problem
Can you solve my problem ?
- Yes, we are specializing in DDoS Protection, so you can surely count on us to help keeping your business online !
How does our technology works against DDoS Attacks ?
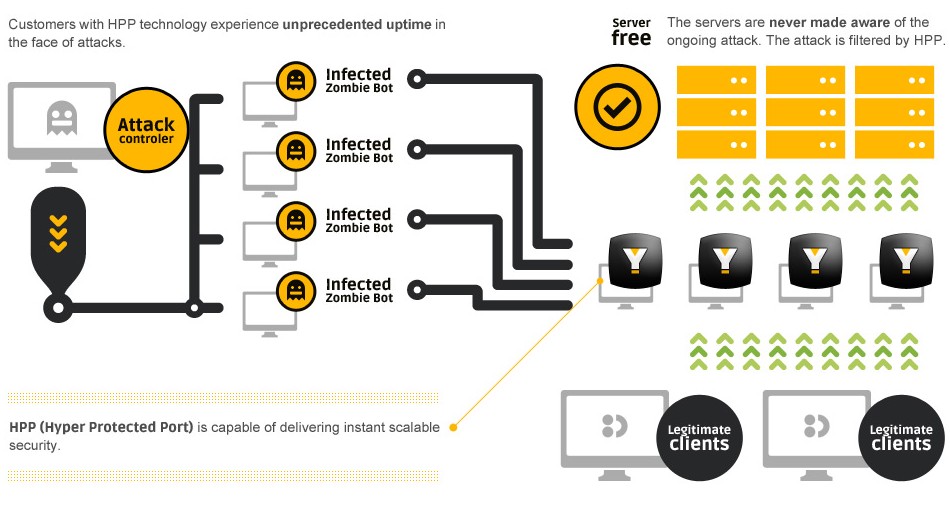
- For websites, the traffic will pass through our mitigation network where it is divided into two different layers, the frontend layer and the backend layer.
In the frontend layer, we’ll inspect and drop automatically any malicious traffic in the Layers 3 and 4.
At the backend layer, we’ll inspect the user data at the application layer (Layer 7), with our exclusive patent pending HDS – “Human Detection System” - The HDS is capable of identifying and automatically allowing your traffic to be sent only to legit requests, reducing alot the overhead caused by a Layer 7 attack.
- We have custom algorithms to verify the reputation of IP Addresses or Subnets to know based on their unique behavior who is a legit user and who is a zombie bot.
- In the picture shown below, you can see how our system will act against any ddos attack.
Reasons to choose our company
- Be protected 24h against all known DDoS attacks;
- Free Setup
- Support with our DDoS specializing engineers.
- Low false positive rate.
- Good latency and response times.
- Premium Bandwidth (Our traffic is always processed first by the carriers).
- Decent pricing becoming the best deal, considering our quality and advantages.
- Tier 2 own infrastructure, high end mitigation hardware and network with high availability.
Link References and Documentation
Do you want to learn more about DDoS Attacks ?
To see extra informations about the:
- TCP DDoS Attacks, click here.
- UDP DDoS Attacks, click here.
- ICMP DDoS Attacks, click here.








