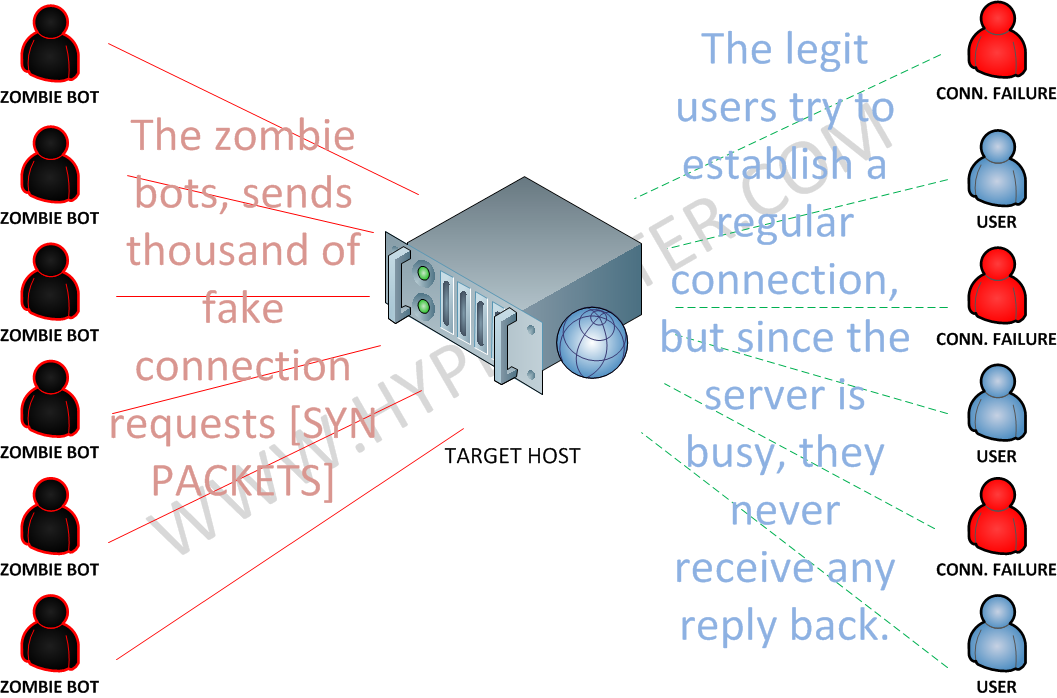
How does this attack type works ?
- Basically, this attack is meant to consume all available server resources, by overwhelming the control/state tables of the target host OS.
What does it means in practical terms ?
- Within this attack type, generally your server will just become unavailable for any type of external request that try to legitimately connect to any of your services.
- Many connection attempts are forged, confusing the host, making it believe that many of requests are real requests making it to serve to them up to its limit.
- In this case, while this attack is being performed, you will notice a high cpu, network and memory usage. In any packet sniffer such as wireshark, the packets will contain the SYN flag in all them.
- The zombie bots in the example, can either be infected regular user computers or compromised servers in any organization.
- You can learn more about this tcp attack : clicking here
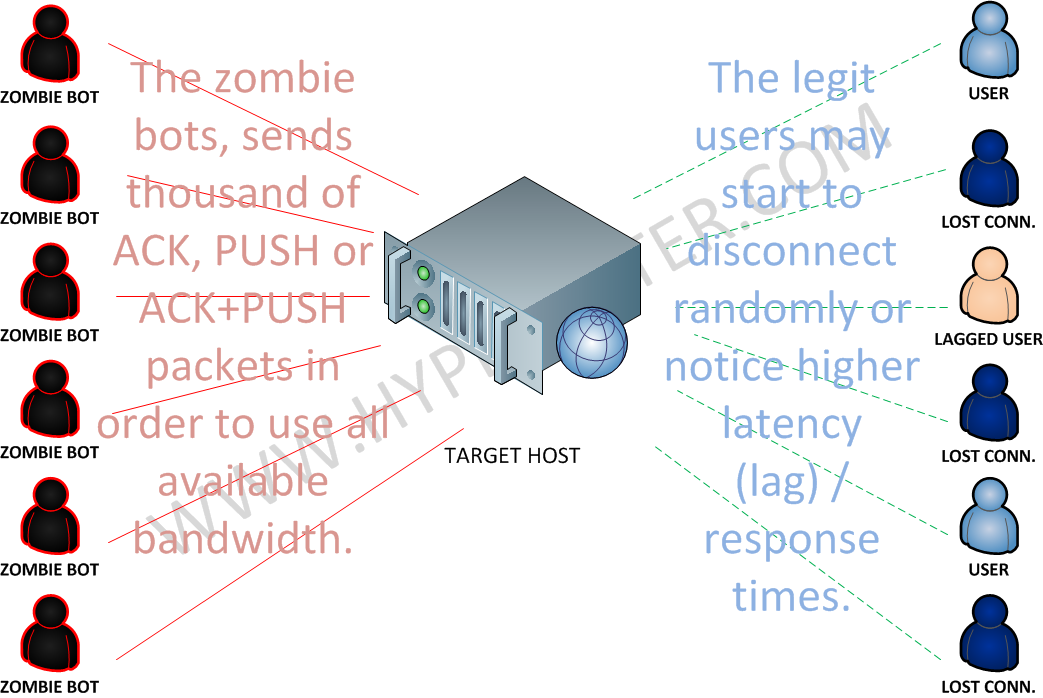
How does this attack type works ?
- Similar to an UDP Flood, this attack is aimed at consuming the most bandwidth as possible in the target host.
What does it means in practical terms ?
- You will notice from just a bandwidth utilization up to entire networking capacity being used in the target host.
- There must be lag spikes, higher response times and disconnections caused during this type of attack, due to lack of networking bandwidth.
- There won’t be a higher cpu utilization, except in cases where the amount of received packets, may exceed the system I/O capabilities.
- The zombie bots in the example, can either be infected regular user computers or compromised servers in any organization.
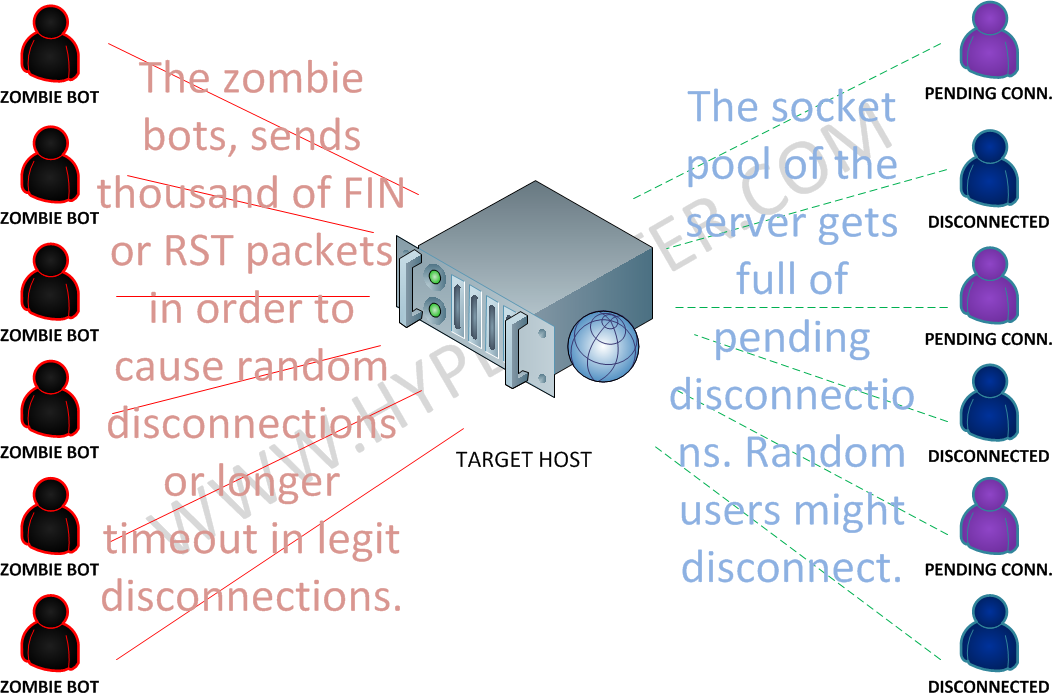
How does this attack type works ?
- Used to cause light overwhelming of control state tables of the target host OS.
What does it means in practical terms ?
- There is a chance where in case the attacker guesses users IPs and sequences to randomly start disconnecting them.
- There won’t be a higher cpu utilization, except in cases where the amount of received packets, may exceed the system I/O capabilities.
- The zombie bots in the example, can either be infected regular user computers or compromised servers in any organization.
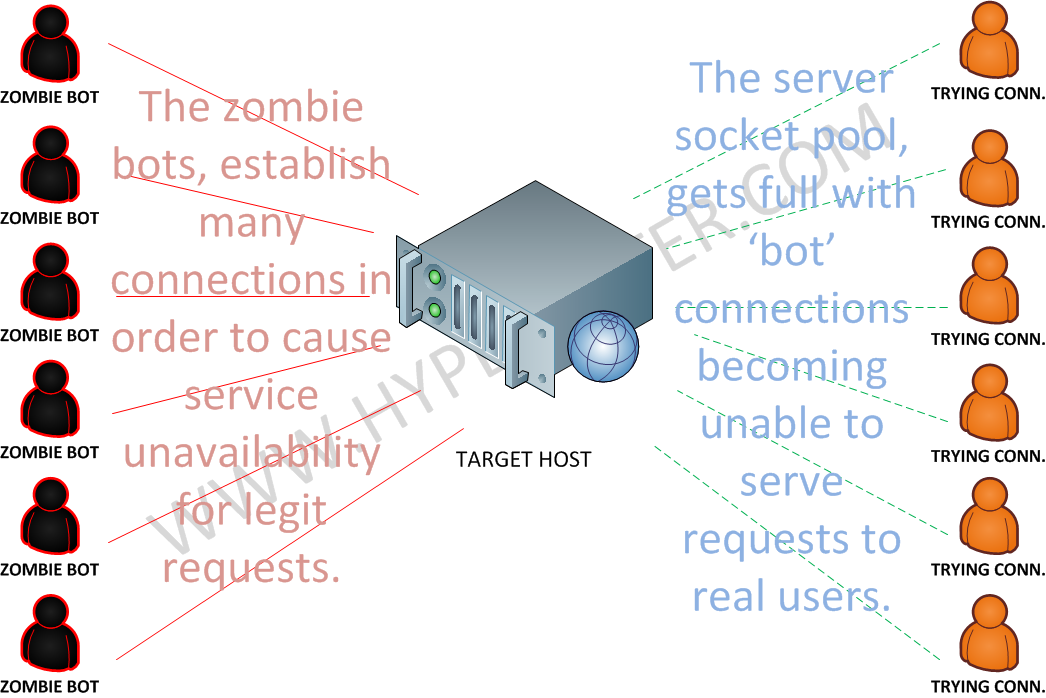
How does this attack type works ?
- Used to flood an application or OS socket pool in the target host, until it becomes full and unavailable.
What does it means in practical terms ?
- The application pool, will get full, causing it to crash or not accept any other connections during the event.
- Can cause the target host stack/pool to get full, up to the point it will not accept any connection from the outside at all.
- The zombie bots in the example, can either be infected regular user computers or compromised servers in any organization.
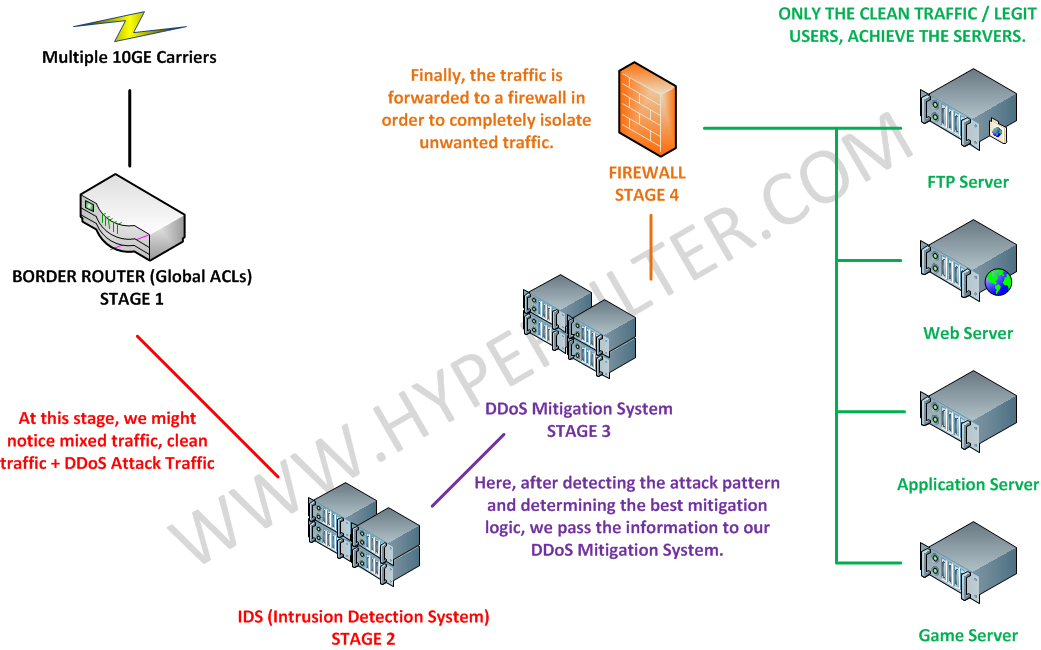
It is easy, we have specializing engineers in the DDoS Mitigation area !
- We are used to solve these types of attack daily with our customers, with our automated systems !
What does it means in practical terms ?
- Generally these DDoS Attacks are solved with a quad stage mitigation system as shown in the picture.
- There aren’t any noticeable latency constraints with the usage of our DDoS Mitigation technology.
- We have a large know-how in this area, which means you can be safe, that whenever a new issue raises our team will be able to solve it !
HyperFilter DDoS Protection SolutionsHyperFilter DDoS Protection Solutions
2013-08-25 17:00:31-05:00
2016-09-18 10:07:28-05:00