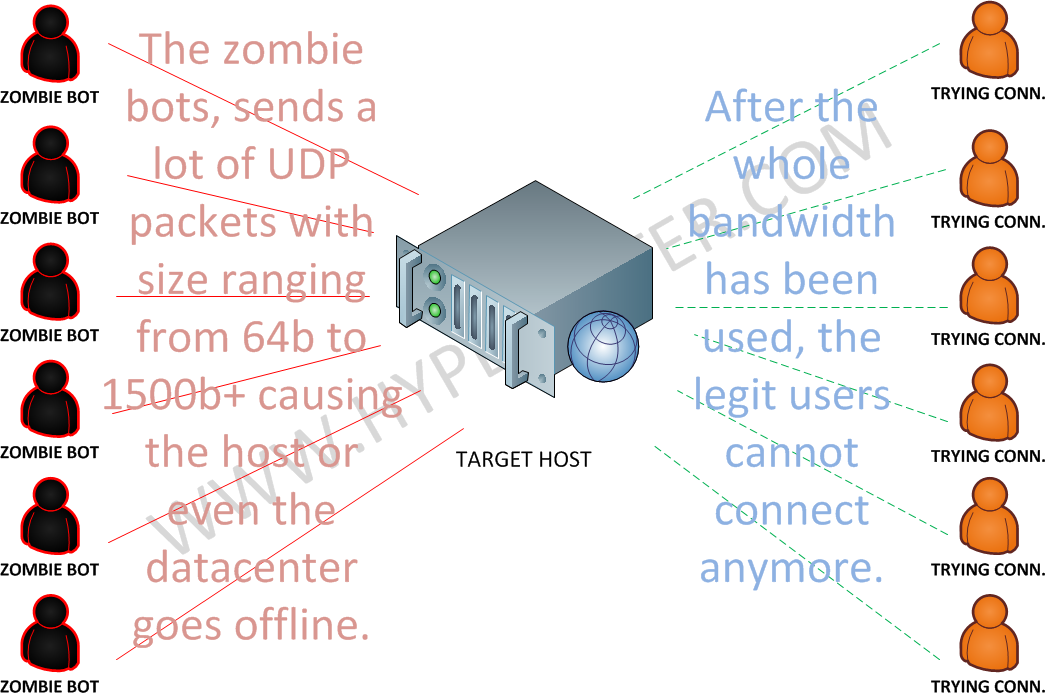
How does this attack type works ?
- This is an attack focused to be consuming all the available bandwidth of the target host.
What does it means in practical terms ?
- Within this attack type, an attacker can potentially consume all the available bandwidth capacity in the target host or even in the datacenter.
- There are variants, where this attack is made to become packet intensive, causing routers or switches to start failing to serve the network.
- Other variantes of this attack, are meant to cause issues with specific UDP Applications.
- The zombie bots in the example, can either be infected regular user computers or compromised servers in any organization.
- You can learn more about this udp attack : clicking here
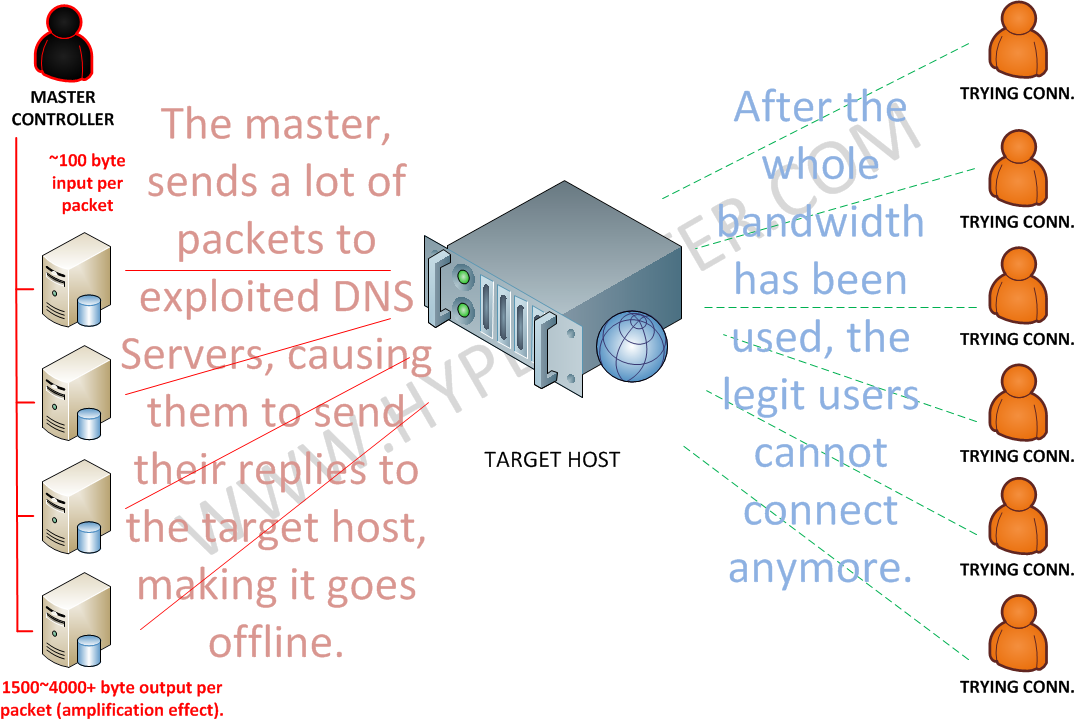
How does this attack type works ?
- Another attack focused to be consuming all the available bandwidth of the target host.
What does it means in practical terms ?
- The main difference with this attack type, is the hability to amplify the attack strength by using exploitable DNS Servers on the internet.
- An attacker will search and make a big list containing the exploitable DNS Servers, with this data he will be able to control a ‘virtual’ network of exploited servers.
- Within a master server, he will send forged packets, with the target host IP as requester (source spoofed IP), making all the DNS replies to be sent to the target host.
- This will cause the host to get down easy, with the amount of bandwidth in use, up to 64x or more, than the original used bandwidth to launch this attack.
- The zombie bots in the example, can either be infected regular user computers or compromised servers in any organization.
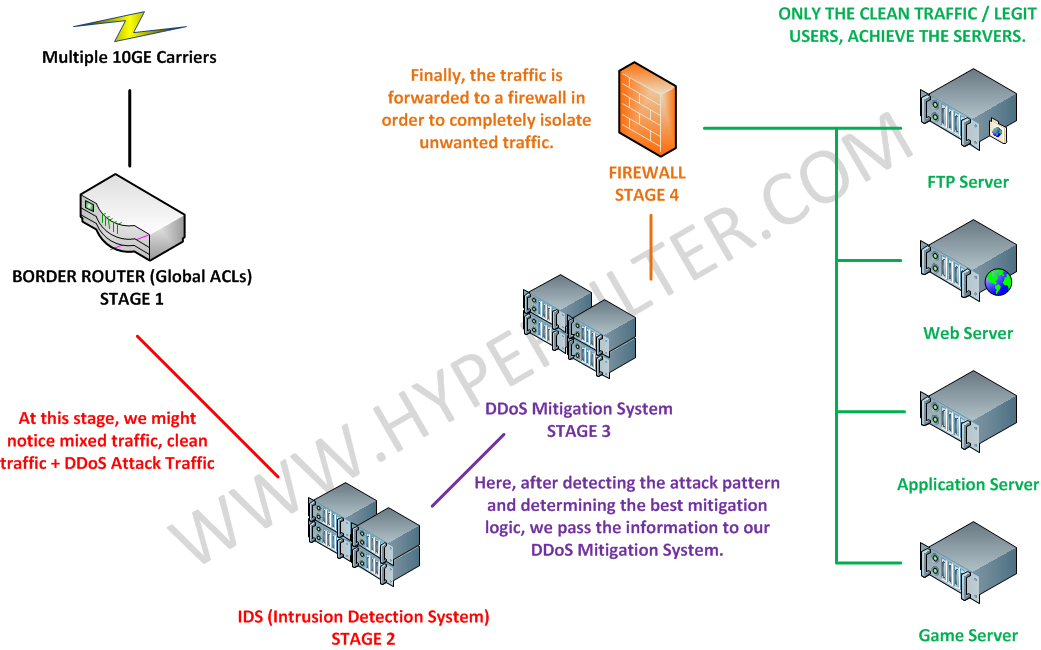
It is easy, we have specializing engineers in the DDoS Mitigation area !
- We are used to solve these types of attack daily with our customers, with our automated systems !
What does it means in practical terms ?
- Generally these DDoS Attacks are solved with a quad stage mitigation system as shown in the picture.
- There aren’t any noticeable latency constraints with the usage of our DDoS Mitigation technology.
- We have a large know-how in this area, which means you can be safe, that whenever a new issue raises our team will be able to solve it !
HyperFilter DDoS Protection SolutionsHyperFilter DDoS Protection Solutions
2013-08-25 17:00:01-05:00
2016-09-18 10:07:18-05:00